 Print
Print
KDDI R&D Laboratories Achieves World’s First Practical Application of Personal Information Protection Technology to Enhance IoT Security Combines Deployable Data Size and High Speed Processing for IoT
September 30, 2015
KDDI R&D Laboratories, Inc.
SAITAMA, JAPAN, September 30, 2015 — KDDI R&D Laboratories, Inc. announced today that it has developed software technology to protect personal information and other critical data for IoT and other uses, and has put the technology to practical use.
The practical use of the method to protect the in-memory key data for encryption is the first of its kind in the world*1.
This research is partially supported by the Japan Science and Technology Agency’s “The Security Infrastructure Technology for Integrated Utilization of Big Data,” one of the JST Strategy Creative Research Promotion Programs.
Background
In recent years, cyber-attacks have caused numerous instances of personal information leaks. Encryption protects the data in the storage; however, the data encryption key (DEK) cannot be sufficiently protected by existing encryption technology. This technical restriction has led to a growing number of information leaks from DEK due to cyber-attacks targeting in-memory data.
Furthermore, more personal information is being uploaded to networks with cloud service expansion and IoT penetration, meaning that it is essential to have security measures that cover various types of devices.
Technology Overview and Results
This technology applies KCipher-2 high-speed stream cipher,*2 a software technology developed by KDDI R&D Laboratories that protects in-memory data. By combining our encryption technology and software protection technology, in-memory DEK is distributed and mixed with dummy data. Only authorized users can read the DEK correctly; thus, the technology provides high grade of security. Compared to an existing implementation,*3 this technology achieves about ten times the processing speed. Further, it can be implemented as light-weight and four kilobyte-size software, it is feasible even for resource-limited devices.
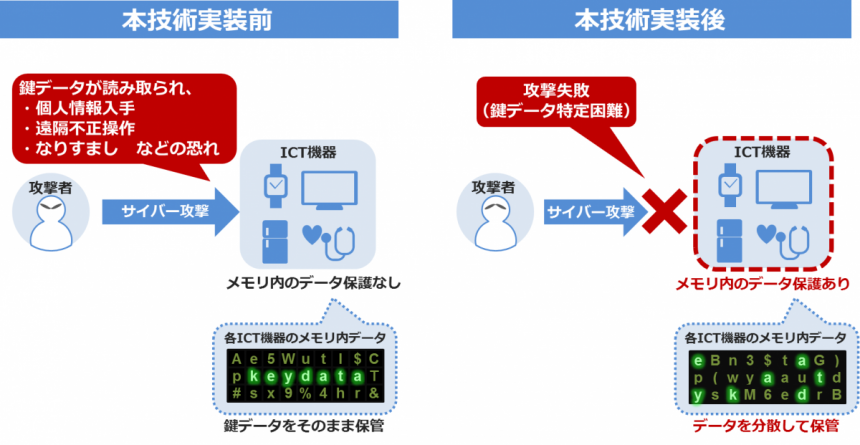
Image of this technology
Usage of this technology
This technology is being used for verification of customer information with dedicated “au WALLET Welcome Gacha!”*4 terminals installed in au Shops.
We hope that this technology will be used in cloud services and smartphones that require high grade security, as well as for IoT, which holds various types of personal information including lifelogs and payment information.
KDDI R&D Laboratories’ world leadership in the field of security is proven by accomplishments such as the development of KCipher-2, which was selected as an e-Government recommended cipher, and its world-record-setting results*5 in a next-generation cipher breaking contest. The Company continues to engage in cutting-edge research and development to help realize an ever safer and more secure society.
END
*1: As of September 30, 2015. According to KDDI R&D Laboratories’ research.
*2: March 26, 2013 press release, “KDDI R&D Laboratories High-Speed Streaming Cipher KCipher-2 Selected as an e-Government-Recommended Cipher”
*3: Comparison made with Oblivious RAM Library v0.1 as the conventional method http://web.rememberingemil.org/Research/ObliviousRam/ObliviousRam.html
*4: A service in which users win presents of WALLET points by waiving their au WALLET Card or au WALLET Credit Card over dedicated terminals in au Shops
*5: July 19, 2013 press release, “KDDI R&D Laboratories Achieves World Record at Contest in Breaking Next-Generation Encryption”
※The information contained in the articles is current at the time of publication.Products, service fees, service content and specifications, contact information, and other details are subject to change without notice.